Impacted organizations have until January 2025 to become fully compliant with the EU’s Digital Operational Resilience Act. Dr. Roland Pulfer looks at what needs to be taken into account and how to successfully and pragmatically make the changes required for compliance.
The EU’s Digital Operational Resilience Act, or DORA for short, came into force on 17 January 2023. 24 months later, by January 2025, financial institutions and ICT third-party providers must meet the new requirements for the operational stability of digital systems.
Cyber hazards have been at the top of companies’ ranking lists for several years in a row. The financial sector is particularly attractive for cyber criminals. According to a 2019 study by the Boston Consulting Group, banks are attacked 300 times more often than companies from other industries. Furthermore, attacks are seeing a sharp increase and are becoming increasingly ‘intelligent’.
Moreover, if you take into account the fact that – according to the latest report by IT security specialist Trend Micro – financial institutions are the most common payers of ransom money to cyber extortionists, it is clear that the financial industry faces an exceptionally high risk from cyber threats and thus an exceptionally strong obligation to face these risks with excellent preparation, comprehensive concepts, intelligent technical assistance, and effective teams.
With DORA the EU has created international guidelines for protecting the financial IT landscape and unifies existing European and national policy.
DORA – what is it about?
Now that DORA has come into force, all financial service providers must prove that their organization can withstand many different ICT crises across levels and departments and that the operational stability of digital systems is consistently ensured. As a result, it brings into focus the ability to fend off cyber risks and the ability to act in an emergency.
Depending on the size of the company and the risks posed by the business model as well as the respective financial company’s degree of digital operational resilience, it will be necessary to strengthen many skills in risk management or perhaps acquire new ones while keeping proportionality in mind. Specifically, organizations must ensure the following:
- Risk management is made into a top-level issue: DORA stipulates that management must assume specific responsibility for IT security. Managers must comprehend the consequences of various risks and the expectations set for them. Apart from legally required continuing education on IT risks, they are obliged to carry out a risk assessment not only for their own company but also for all third-party vendors. They must define managers, authorise business continuity and restart plans, authorise audits and adequately inform themselves about ICT incidents as well as collaboration with third parties. This also includes building quick information pathways, ideally making important information consistently up to date. Therefore, DORA requires companies to make ICT risk management a top-level issue.
- Specifically and continually identify risks: companies must be familiar with their security goals and regularly readjust them. They are obliged to consistently monitor all systems and interfaces for anomalies 24/7, detect and evaluate discrepancies, and document risks.
- Respond swiftly: in an emergency, organizations must be able to immediately respond to an attack or an anomaly and carry out the appropriate countermeasures. The same applies for implementing emergency prevention, managing restoration plans, and reducing risks.
- Communicate professionally and strategically: smooth, secure, and direct – the new regulation sets high requirements for processes and structures for communicating with the relevant internal and external target audiences. One important goal is the fast flow of information. As a result, incidents must be fully documented and communicated internally as well as externally in order to disseminate knowledge. In severe cases, there is now an official reporting obligation for the entire financial industry – not just for major institutions.
- Comprehensive testing and training: companies must prove that their systems, data, and processes are always up to date. To that end, they are required to perform robust and comprehensive tests on digital operational stability (Operational Resilience Testing). Furthermore, Threat-Led Penetration Tests (TLPT) are required at least every three years, i.e., a company’s cyber resilience must be tested via a simulated attack from what is known as an ethical hacker.
Ultimately, all the requirements are geared towards ensuring that the parties responsible can make fast, informed, decisions in critical situations and that they are resilient, i.e. prepared for alternatives. This is because DORA requires a holistic view – virtually a perspective of a company’s blueprint.
So, what do you need to do to strategically position your own organization and make it resilient against cyber hazards?
Optimise the data situation: ensure high availability, topicality, and quality
The most important foundation is a solid database with high data quality, data availability, and interconnection. You can only take the right path to your goal if you know where you stand. However, what may sound simple is immensely challenging in many companies. On the one hand, this is because data are often stored in silos and are not very detailed in their own right. On the other hand, it is because data are not even recorded at all or are not maintained up to date. For instance, an important factor for implementing the DORA regulation are performance data from IT systems, data on the threat landscape, and the criticality of various processes and systems as well as information on incident response plans with escalation hierarchies and communications strategies. Having a perspective of your own company’s horizon is an important core criterion. Can managers easily verify which vendors meet the DORA requirements? Do they have an up-to-date view of the overall global hazard situation? Even seemingly simple things should be thoroughly reviewed again. Is there complete and up-to-date contact data for all relevant people who must be contacted in case of an ICT emergency? Is there an overview of people who possess important know-how in the company? Details such as these things make a difference in an emergency.
Documenting intelligently: Identify relationships, act with purpose
A solid database is the necessary foundation. However, it will not become a useful work tool until the data is intelligently interconnected. Correlations, dependencies, assignments – the database needs to be organized and structured. In other words, processes, and procedures must be identified, classified, and documented in a manner that makes them easy to update and interconnectable in increasingly new combinations.
If data is intelligently interconnected, then not only does it provide useful insights but also allows for processes to be automated – thereby easing the burden on the organization.
Rule-based data repositories give logic to the data and ensure that all the links are individually tailored to the needs of the company. For instance, if there are incident response plans in digital form that are linked to the contact data for the corresponding teams, then automatic workflows can be initiated. Or if system data from proprietary systems is linked to live reports from cyber warning services, then automated alarms can be triggered, or monitoring, evaluation, control, or verification rules of any kind can be initiated.
It is exceptionally helpful to digitally record the DORA regulation itself and then interconnect it to the business architecture – from processes and roles to applications, customers, and vendors. Doing so enables gaps and weaknesses to be scanned and the regulatory risk to be determined. Data also exists in such a repository free of redundancy. Not only does this reduce the required maintenance but it also eliminates sources of errors.
However, a database is only as good as how it is currently maintained. Therefore, it is important to ensure that data are not only intelligently interconnected but also easy to maintain and document. If the data source is outside or in another system, then intelligent connection ensures consistency.
User-friendly input screens, comprehensive interfaces to existing systems, and automatic querying of the latest data are essential for making up-to-date and forward-looking analyses. Ideally, the infrastructure is created in a way that the data can also flow in reverse, i.e. from the comprehensive database back to the original systems to reduce the amount of management required there as well.
Detailed visualisation: one image of the situation – many perspectives
Even if a lot can be automated nowadays, in the end, it is people who make the important decisions. Therefore, data and information should be available in a ‘human-readable’ form, appropriate for its target audience. It is important for the visualisation to be made in as many diverse and unique ways as possible so that every decision-maker can receive input that is ideal for how they think and work.
Tables, matrix views, workflows, or trend charts – the better the visualisation, the faster and more purposeful the action. Because of this, it is important that systems have the essential characteristics, key figures, data, facts, quality measurement values, aggregations/consolidations, and possible outage impacts available but presented in a way that reduces the complexity for the user.
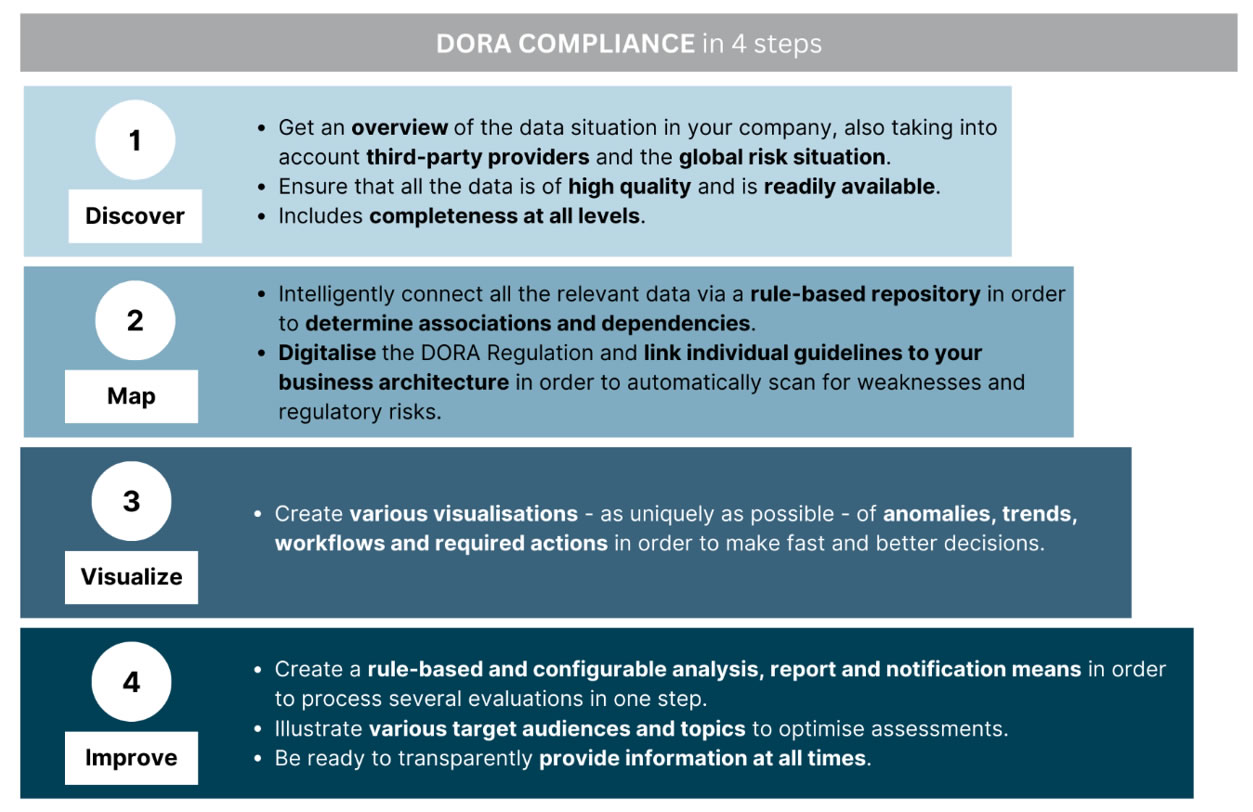
Figure one: Manage data without redundancy and answer all questions from a single source. The following applies for the database in risk management: If they belong together, leave them together.
Manage, evaluate and monitor: the implementation of a compliance requirement always depends on the ability to render the required proof and inspections. There is increasingly frequent overlap between the requirements of different directives and regulations; and DORA is no exception. A structured, interconnected, and intelligent monitoring assessment also helps here.
A rule-based and configurable analysis and reporting system can connect several assessments – from DORA to the GDPR General Data Protection regulation – with each other and handle several requirements with one response – and it can do so spontaneously, periodically, or permanently, manually, as warranted, automatically, or intelligently. Ideally, different target audiences and topics of a company will also form a structured, sustainable monitoring management system (IT, security, finance, legal, etc.)
Conclusion
Intelligent data links can significantly reduce the effort to successfully implement the DORA regulation over the long term. It requires high data availability and quality as well as an intelligent interconnection of existing data via dashboards, graphics, tables, workflows, and alarms. The following holds true for managers: If they belong together, leave them together. As a result, you only need to maintain the information network, i.e. the interconnection of all of the ICT’s relevant architecture assets, once and you will be able to obtain a company DNA that allows you to answer any questions from a single source – from risk, monitoring, security, and emergency prevention to outsourcing, restart, rescission, testing, and simulation of your systems.
The author
Dr. Roland Pulfer, is founder of Business-DNA Solutions GmbH and GRC expert at F24 AG.
Want to learn more?
Join a free DORA web-seminar on Monday, 24th July 2023. This is hosted by Dr. Pulfer as well as resilience expert John Davison (Managing Director F-24 UK Ltd). Find out more at: https://f24.com/en/dora-web-seminar-uk/


